:: 국내 정보보안 솔루션 개발 기업 재직 ::
- 앱 위변조 방지 솔루션 : 미들웨어 담당 / 해킹 대회 운영진 / 국내 유명 해킹/방어 훈련장 제작
:: 국내 정보보안 전문 업체 재직 ::
- 블랙박스 모의해킹 / 시나리오 기반 모의해킹 / 웹 취약점 진단 / 모바일 취약점 진단 / 소스코드 취약점 진단 / APT 모의 훈련 / DDoS 모의훈련 / 인프라 진단 / 스마트 가전 진단
- 국내 대기업, 중소기업 다수 진단
:: 외부 교육 및 활동 ::
- 멀티캠퍼스, 국가 보안 기술 연구소(ETRI)
- 국내 정보보안 업체 : 재직자 대상 "웹 모의해킹 심화 교육" 진행중
- 해커팩토리 문제 제작
:: 취약점 발견 ::
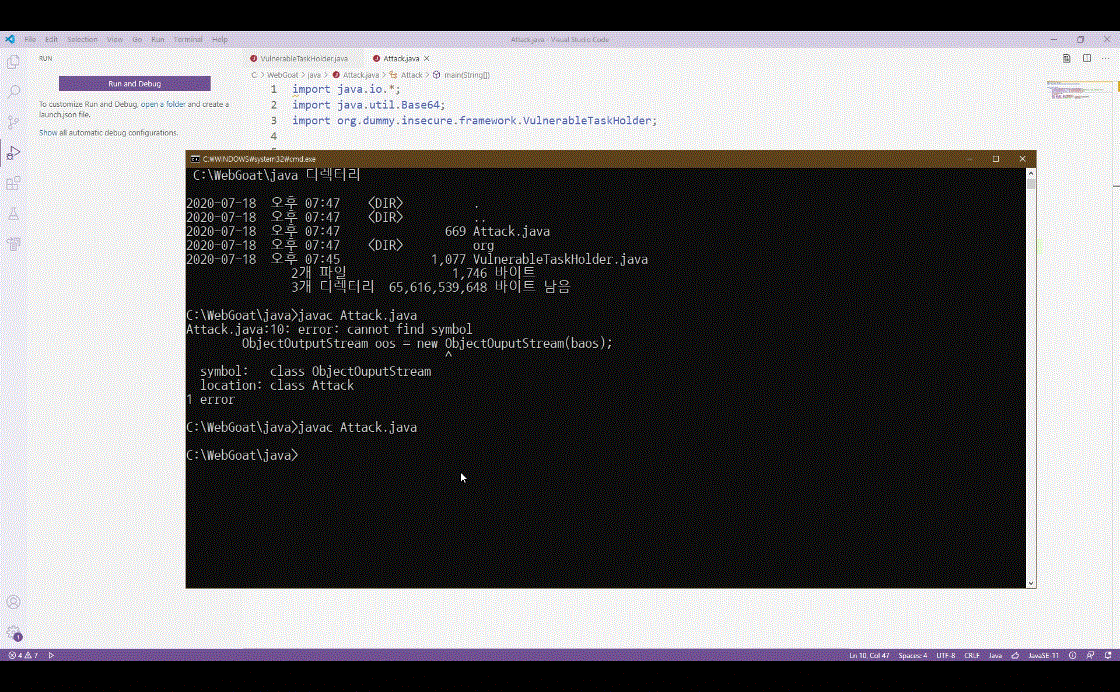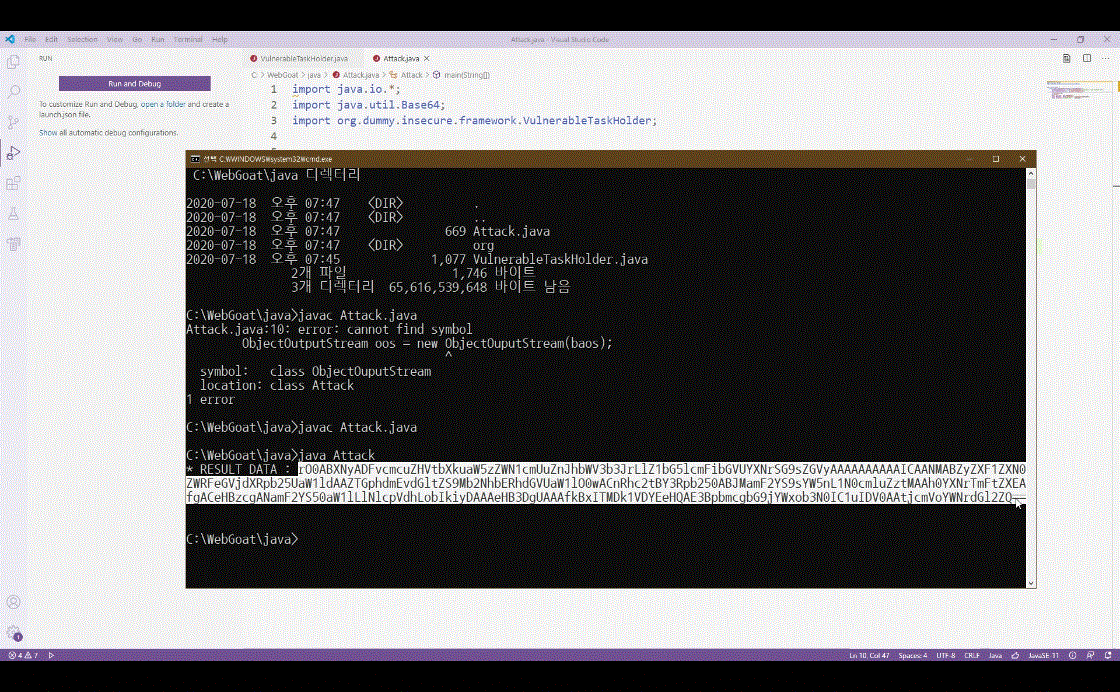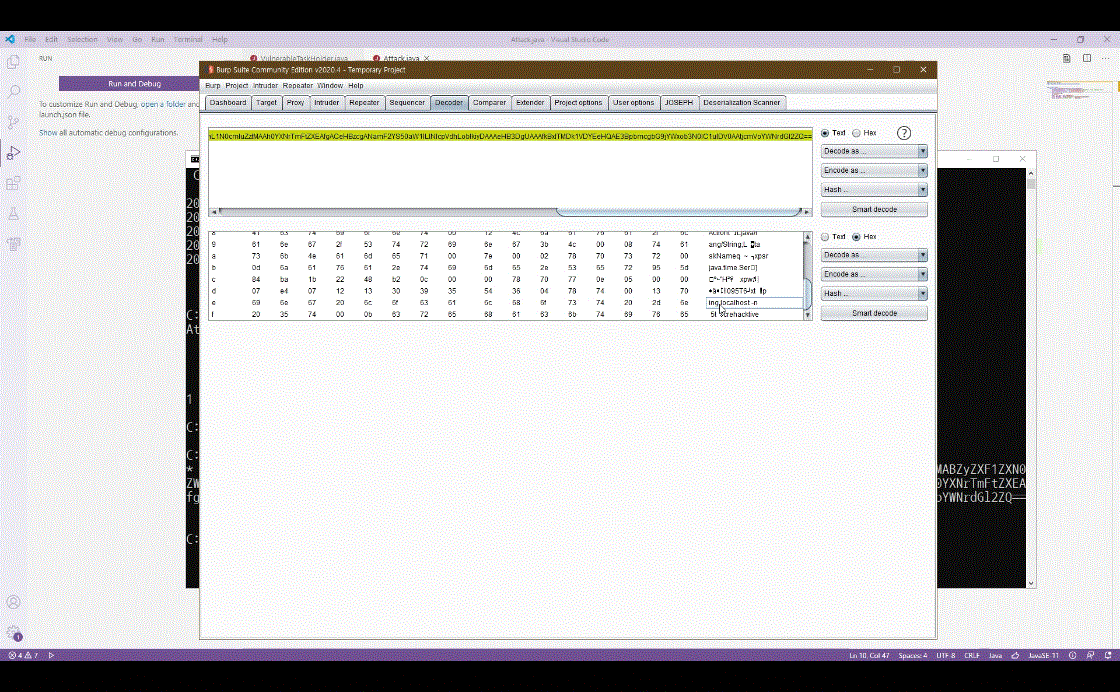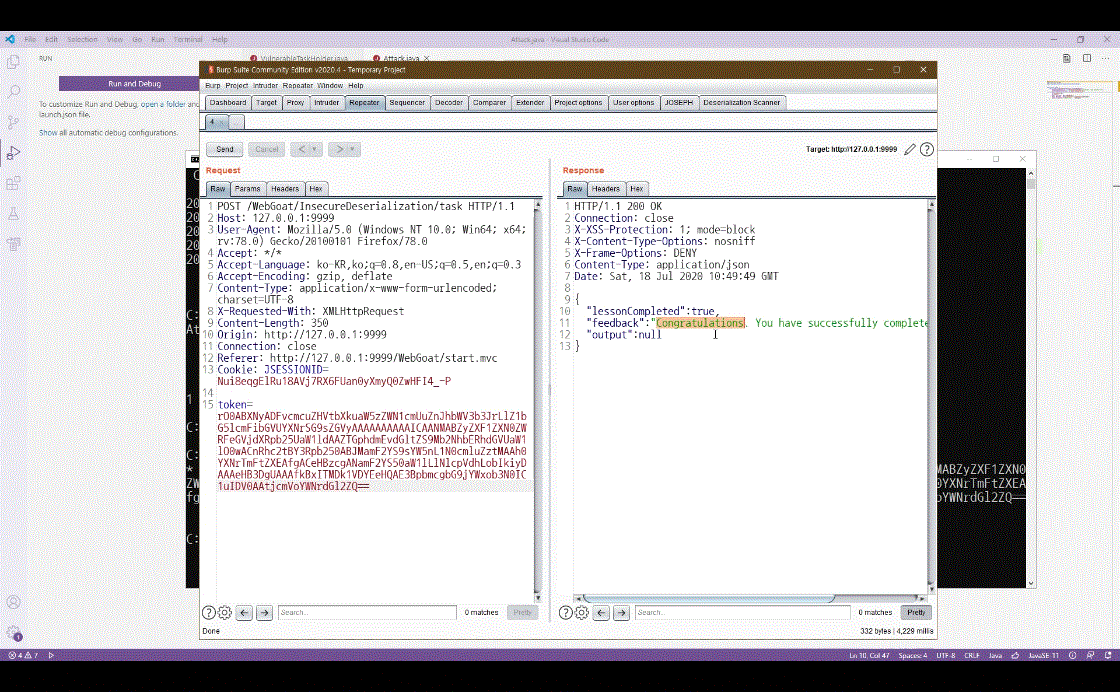
1) Web Application Server 취약점
- TMAX JEUS : 원격 명령어 실행 취약점(Remote Command Execution Vulnerability)
- IBM WebSphere(CVE-2020-4163) : 원격 명령어 실행 취약점(Remote Command Execution Vulnerability)
2) CMS(Contents Management System) 취약점
- 네이버 스마트에디터 : 파일 업로드 취약점
- 그누보드 : SQL Injection , 파일 업로드 취약점(그누보드4, 그누보드5), XSS ...
- 킴스큐 : 파리미터 변조 취약점 , 파일 업로드 취약점
* 이메일 : crehacktive3@naver.com
* 블로그 : http://www.crehacktive.co.kr





![File Upload Vulnerability Advanced Attack Techniques PART2 [Integrated Edition]강의 썸네일](https://cdn.inflearn.com/public/courses/333012/cover/12bd40e1-1e17-493a-81b9-64ac5fed558e/333012.png?w=420)